Cloud storage: Is it safe?

Many businesses have shifted to the cloud in the past few years. In fact, it’s impossible to talk about optimizing businesses without making cloud computing part of the conversation. For small- to medium-sized businesses (SMBs), the cloud can enable more efficient use of resources in nearly every aspect of their business, as opposed to relying on separate functions and expertise.
It can be hard, however, to understand the hype surrounding the cloud, what it can do for your business, and how you can implement a strategy around it. Additionally, security issues are still considered a major factor that keeps businesses from integrating the cloud. Even after your company has adopted it, you still need to think about how to improve your cloud security practices and toolsets.
Cloud computing is definitely affordable, efficient, and scalable, making it the best solution for most SMBs. But without taking the proper precautions, it can still leave you vulnerable. Here’s a quick look at the most common cloud computing security risks:
- Employee negligence– This is particularly dangerous with cloud solutions, as remote workers who log in from their devices could potentially leave the system vulnerable to many outside threats via insecure access points.
- Distributed-denial-of-service (DDoS) attacks– With the proliferation of smartphones, internet of things (IoT) devices, and other computing technologies, DDoS attacks have greatly increased in viability. If enough traffic is initiated to the cloud, your entire network can go down. This could result in a loss of revenue, customer trust, and brand authority.
- Data breaches– Inadequate data backups and improper data syncing could render systems vulnerable to threats like ransomware, a threat that locks and encrypts files. Traditionally, IT professionals have great control over their network infrastructure and physical hardware to secure proprietary data. However, in public, private, and hybrid cloud setups, some of these controls are relinquished to a trusted partner, which is why choosing the right vendor is vital to overcoming this challenge.
- System vulnerabilities– The cloud can still be vulnerable to data breaches, especially in networks that have complex infrastructures and multiple third-party platforms. Once a vulnerability becomes exploited, this could be easily used against an organization.
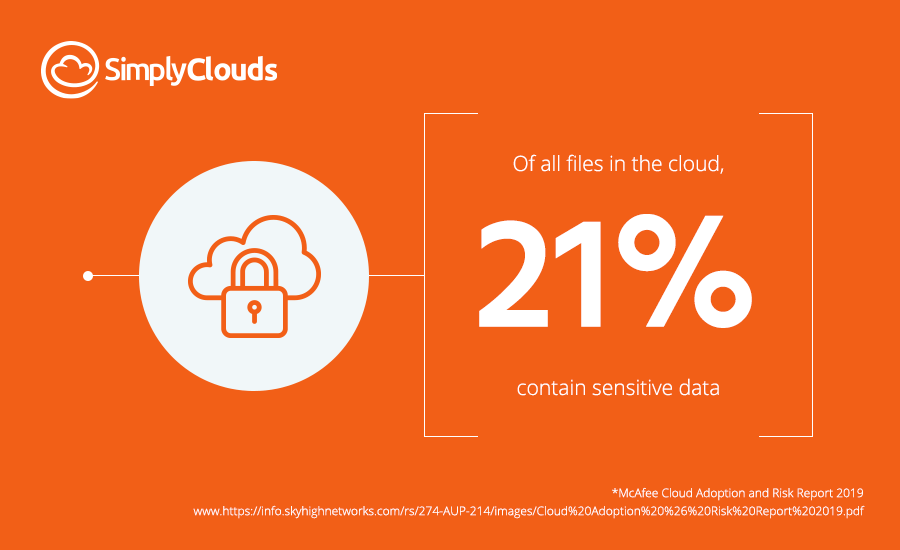
- (N)early a quarter of (data stored in the cloud) requires protection to limit our risk. However, the risk of exposure is counter to one of the key tenets of many cloud services — collaboration… But of course, collaboration means sharing, and that sharing can lead to the loss of our sensitive data.
Source: Cloud Adoption and Risk Report
In spite of these challenges, there is a myriad security measures in cloud computing that surpass the standards of traditional IT. With the right partner, technology, and strategy, you can leverage the benefits of cloud technology and spread the cost of data security for large volumes of customers across multiple data centers. You can allocate more human and financial resources to security measures, including physical, technical, and operational security. Check the following best practices to keep your data in the cloud secure:
Perform risk assessment
If you opt for a hybrid cloud solution, perform an analysis of the type of data you’re handling and evaluate it based on how critical and sensitive it is both for your client and company. Data related to intellectual property must be stored on premises with restricted access only to authorized personnel.
Keep your cloud private
No one outside the local network should be able to access your stored data. Isolate your private cloud from public internet access to prevent attackers from accessing the data via insecure networks.
Be mindful of data handling laws and jurisdiction
It’s wise to choose a cloud provider that provides a data center that physically resides in a region or country in which data storage and handling legislation is favorable to your company’s business interests
Use encryption both locally and in transit
Encrypt any data transfer between the client and cloud service provider. This prevents man-in-the-middle (MiTM) attacks that could intercept broadcasted data. More importantly, any data stored locally or in the cloud should be encrypted to make sure cybercriminals cannot read it in case of unauthorized access.
Backup cloud data
You never know when a disaster may strike. From natural catastrophes like fires or earthquakes to data breaches, it’s best to be prepared. Guarantee business continuity by having ba
Use multiple authentication methods
Implement additional identity verification steps such as SMS authentication or biometric scans so that only authorized parties have access to your data.
Implement security response procedures
Define a set of procedures and policies to handle security incidents. Make sure your clients, employees, and stakeholders understand it and adhere to it. This must include techniques and methods for isolating and remedying security breaches. Also, make sure to review your incident response plan regularly so you can keep up with new and changing regulations, trends, and technologies.
Cloud security should be a multilayered approach, incorporating both security tools and protocols your enterprise employees need to follow. These security protocols help ensure your workers don’t become a security risk themselves. You can also rely on a reputable cloud service provider like SimplyClouds to ensure powerful, reliable, compliant, and secure solutions. Call us today to learn more.
Categories: Cloud backup, Cloud security, Cloud storage
Tags: cloud backup, data security, hybrid cloud, public cloud, private cloud, multi factor authentication, Distributed-denial-of-service attacks, Man-in-the-middle attacks
Share